Overview
- FEITIAN SK Manager tool is a desktop software that can be used to configure the FIDO, PIV and OTP for your security keys.
- Please download the latest version with Hash files for Windows, or macOS, or find history releases here.
- For Windows PIV Usage, please download minidriver and Hash file here.
Get Start
Supported Products List
| Number | Product Name | Supported Application Lists |
| 1 | ePass FIDO Plus | FIDO2 + U2F + PIV + OTP + OPENPGP |
| 2 | ePass FIDO NFC | FIDO2 + U2F + OTP |
| 3 | BioPass FIDO2 | FIDO2 + U2F + PIV |
| 4 | iePass FIDO | FIDO2 + U2F + PIV + OTP + OPENPGP |
| 5 | Multipass FIDO | FIDO2 + U2F |
| 6 | Allinpass FIDO | FIDO2 + U2F |
Functional Description
Home
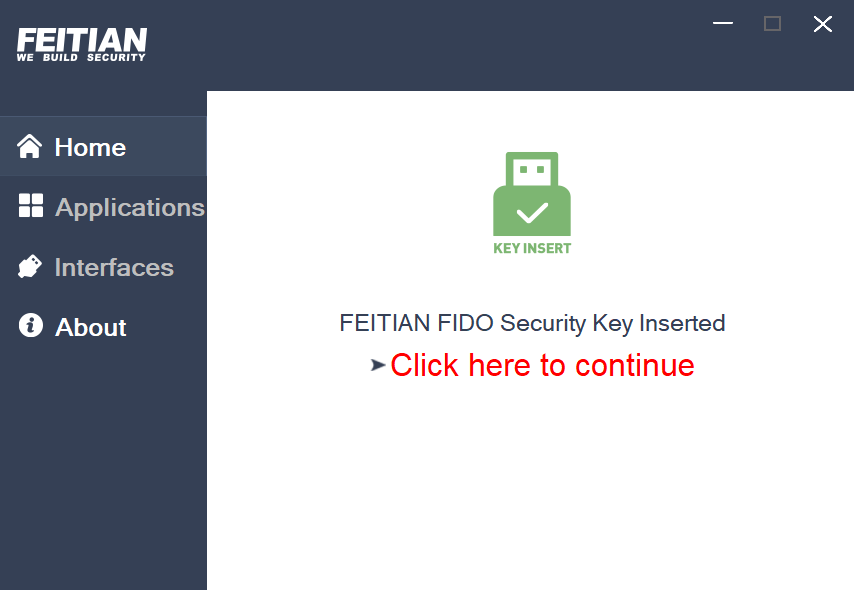
- Open the tool[Run as Admin], it will give a hint to insert the device, after inserting, the tool will show that the key has been inserted and user need to click “Click here to continue”.
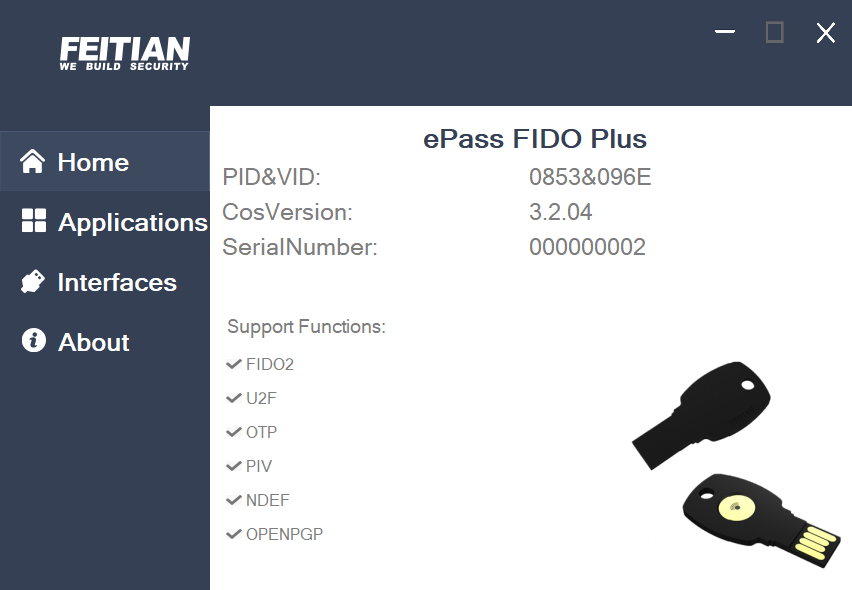
- Using ePass FIDO2 to describe, the following figure shows the home page when user clicks the prompt. Product information will displayed, including product name + PIV/VID + firmware version + serial number.
Applications
- Click “Applications” to display the specific function, mainly with common set functions of FIDO, PIV and OTP, the supported functions are highlighted, unsupported functions are gray and inoperable.
FIDO2
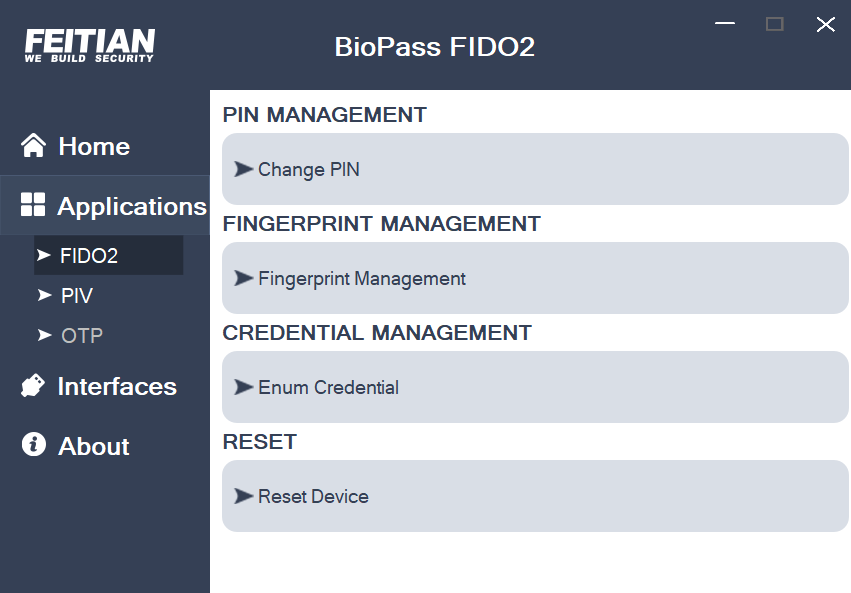
Click “FIDO2” to enter the FIDO2 management page, which includes:
- PIN management, including setting up and modifying PIN
- Fingerprint management(available only for fingerprint supported devices), including registering, verification and deletion fingerprints
- Credential management, including enumerating and deleting credentials
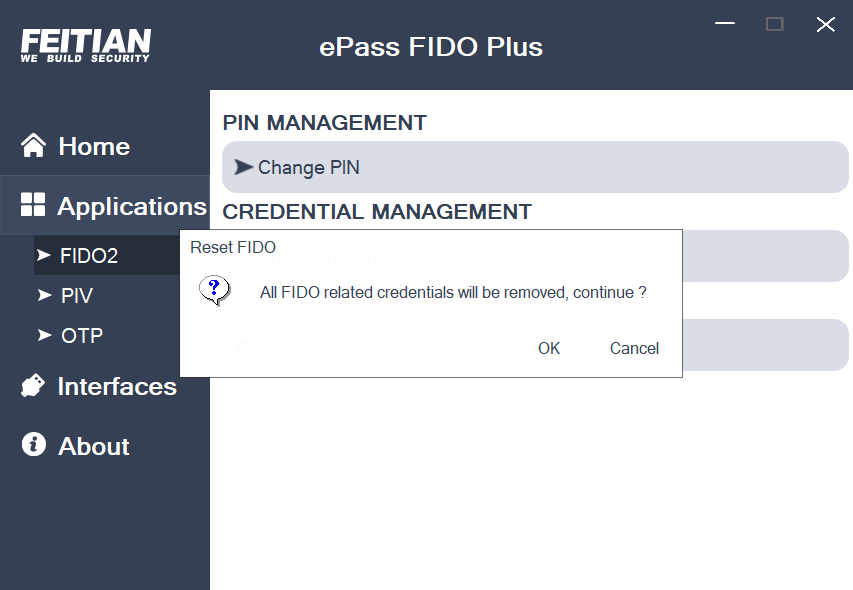
- FIDO2 Reset, removes all reported credentials, fingerprints, and PIN, recover to factory settings
Set PIN & Change PIN
- Click “Set PIN” to setup PIN in the popped-up PIN window, as shown in the figure below.
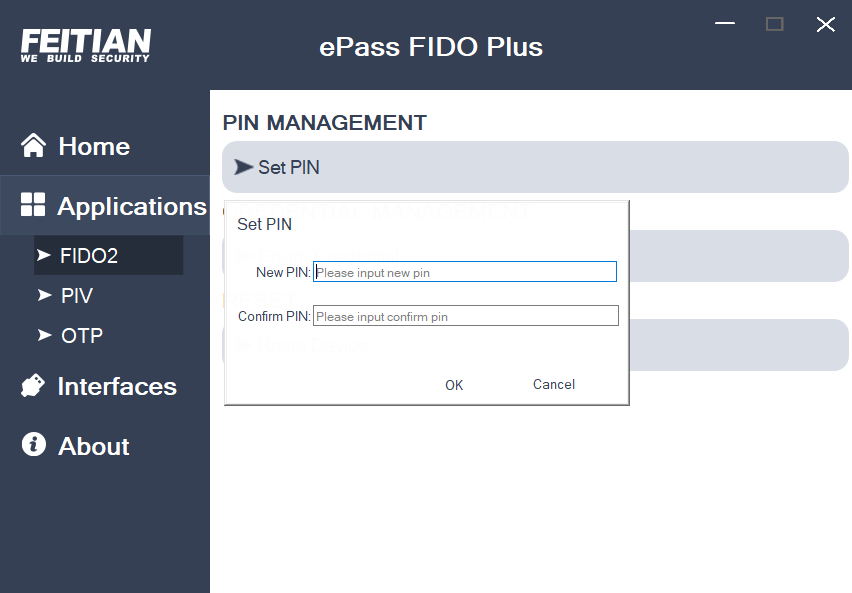
- Note: FIDO2 devices have no PIN at the beginning, but supports PIN setting. The PIN code length is limited to 4-63 digits. PIN check rules are also added, and FIDO2’s PIN supports Unicode character-encoded characters. Non-compliant PIN codes are prompted in a red font. After successful setting up, there will be a hint pop box.
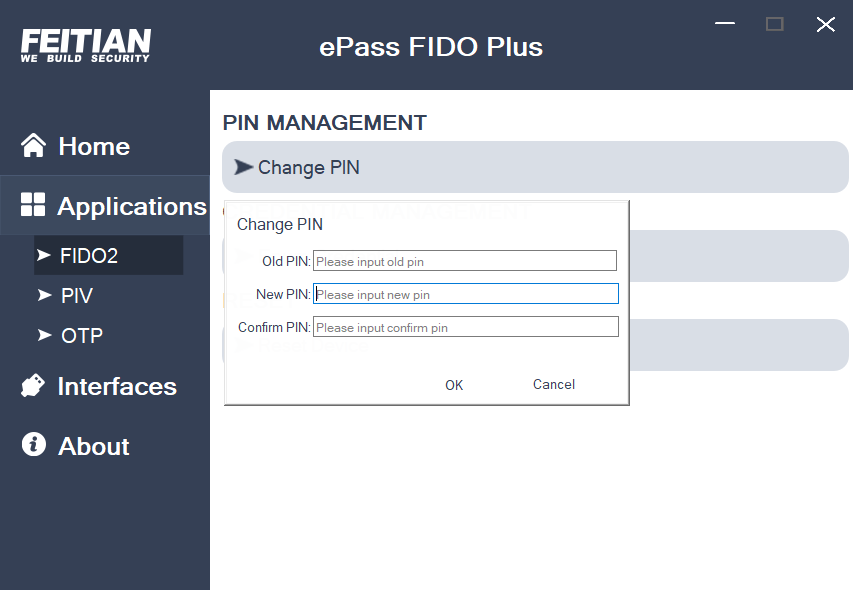
- When the PIN setting is successful, The “Set Pin” button is changed to the “Change PIN” button. You can then modify PIN as shown in the figure below.
Fingerprint Management
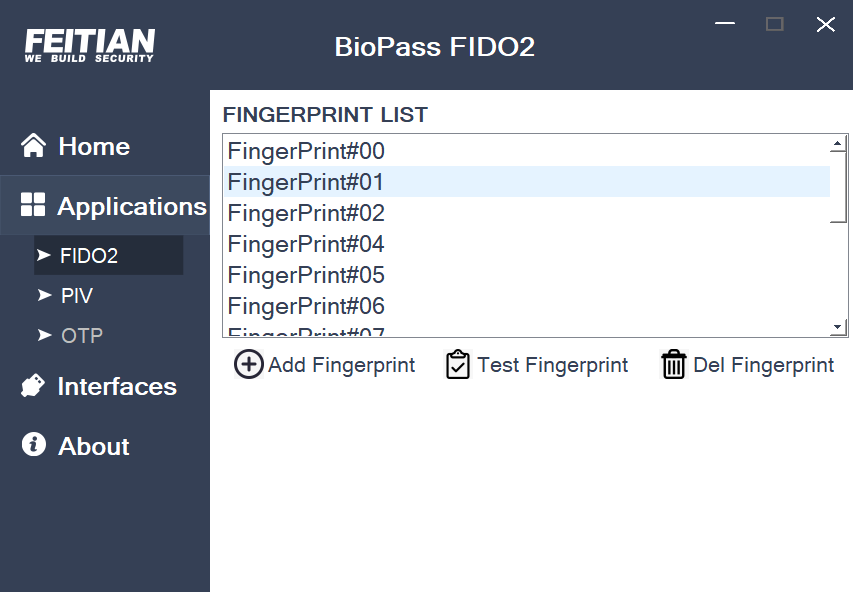
- Click “Fingerprint Management” to enter fingerprint management page. This function is only visible and available for the fingerprint devices such as BioPass FIDO2, You can see list of all fingerprint registered to this device, and the fingerprint functions include adding, deletion and verification.
- Click “Add Fingerprint” to register new fingerprints. Touch the key when its light flashes, enroll fingerprints according to the prompts. The general input times is 4 or 5 times, but different products have different input times.
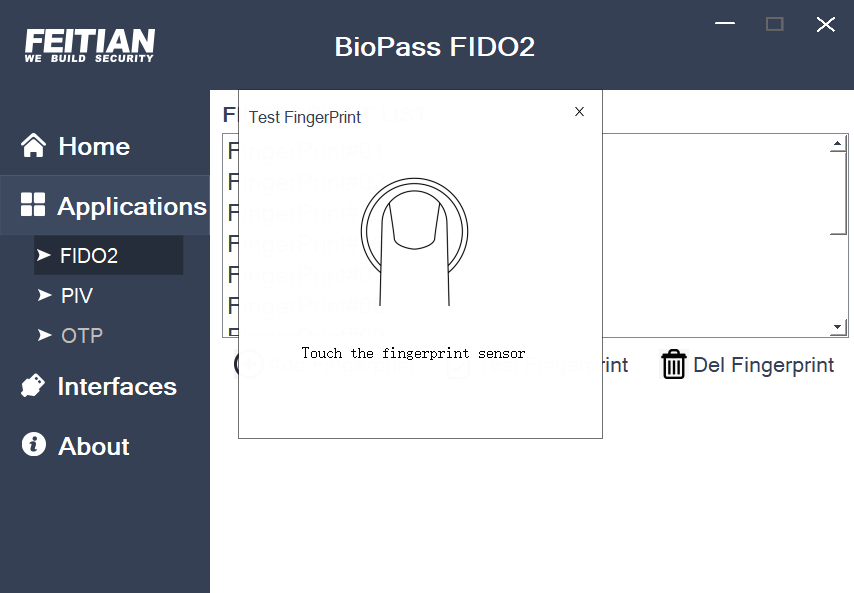
- If the fingerprint is not registered on the device within 10s, an error is prompted, as shown in the figure below. If you want to re-enter, click “Cancel”, and then click “Add Fingerprint” to complete the fingerprint input.
- The new fingerprint will be added to the fingerprint list after successful addition. The fingerprint name will be “Fingerprint#number” (ex, Fingerprint#00), the number will be dynamically accumulated according to the number of inputs.
- Select a registered fingerprint, click “Test Fingerprint” to verify the fingerprint. User needs to touch the key to verity the fingerprint, using an unregistered fingerprint will failed, also if there is no fingerprint detected within 10s, there will be an error output.
- Select a registered fingerprint to delete, and then click “Del Fingerprint”. After completion, you can delete the corresponding fingerprint in the fingerprint list.
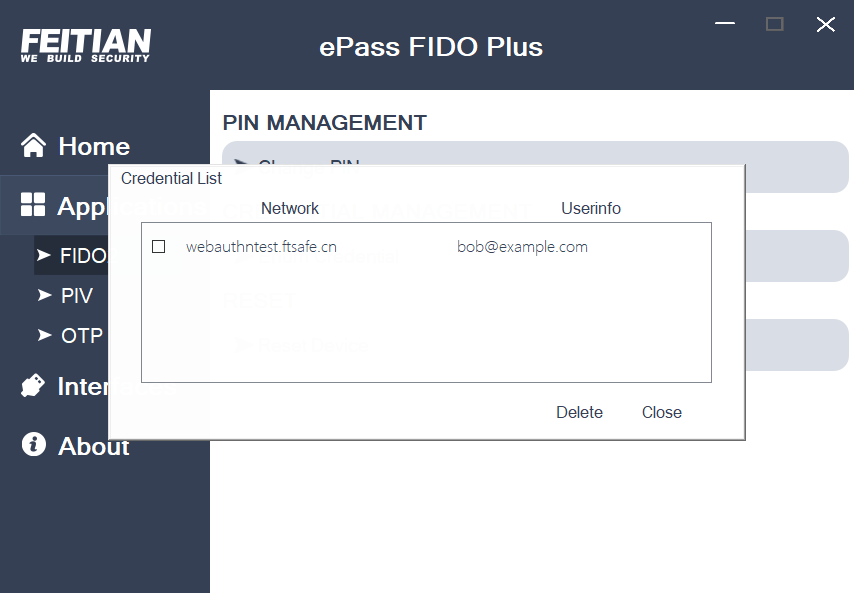
Enumerate Credentials
- Enumerate credential function can manage FIDO2 credentials. Credential management is the management of the credentials stored in the device.
- PIN must be set at first. After setting up the PIN, you needs to verify the PIN before enumerating the credentials in the device.
- Enumeration all credentials for the current device, then select the credentials you want to delete and click “Delete”, to delete the selected credential.
Reset
- Click “Reset Device” to remove FIDO2 configurations of this device, according to Fido2 specification, only within first 10s allows user to reset, if more than 10s, the manager tool will ask user to re-plug the device.
PIV
PIV management functions include:
- PIN management, including management of PIN, PUK and Management Key.
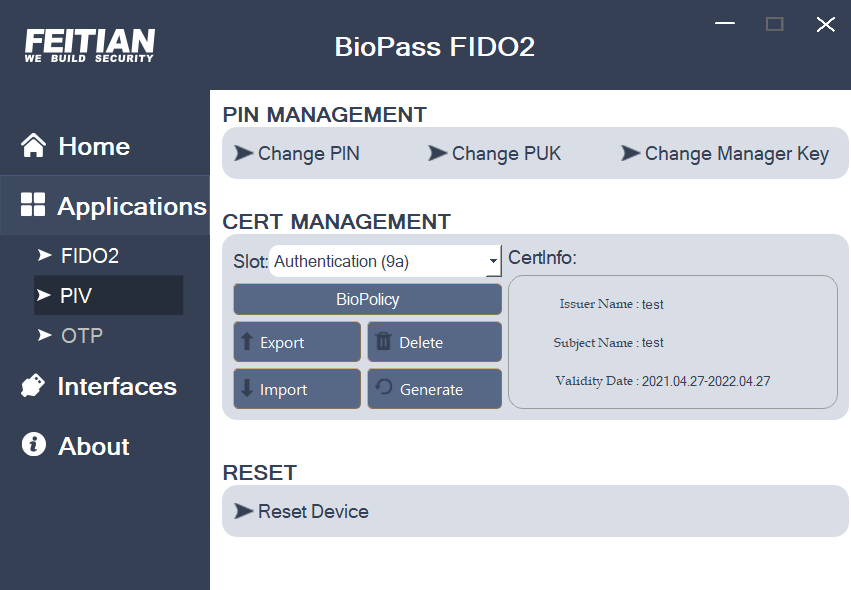
- Certificate-related management(import, export, generate and delete certificates) in different slots (Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)). For fingerprint devices, it also support fingerprint policy for the corresponding slot. Notice that all certificate operations require selecting the slot first.
- PIV Reset, user can restore the default PIN, PUK when the PIV functions are blocked
- The PIV macOS smart card login configuration and unpairing are only available on macOS 10.15 or later.
- In order to use PIV functions on Windows, please download and install PIV Minidriver with Hash file here.
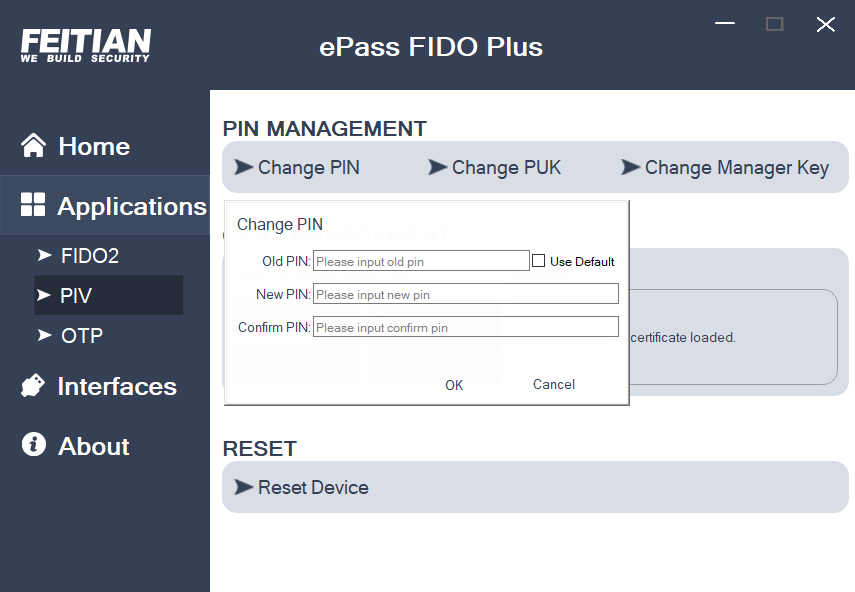
Change PIN
- The default PIV PIN code of our products is 12345678, which can be modified by clicking “Change PIN”. The PIV’s PIN code length is limited to 6-8 digits and only supports numbers. The default retries for PIN is 3, after entering the wrong PIN for 3 times, the PIV function of this device will be blocked. Modifying the PIN must satisfy the rules for the PIV PIN.
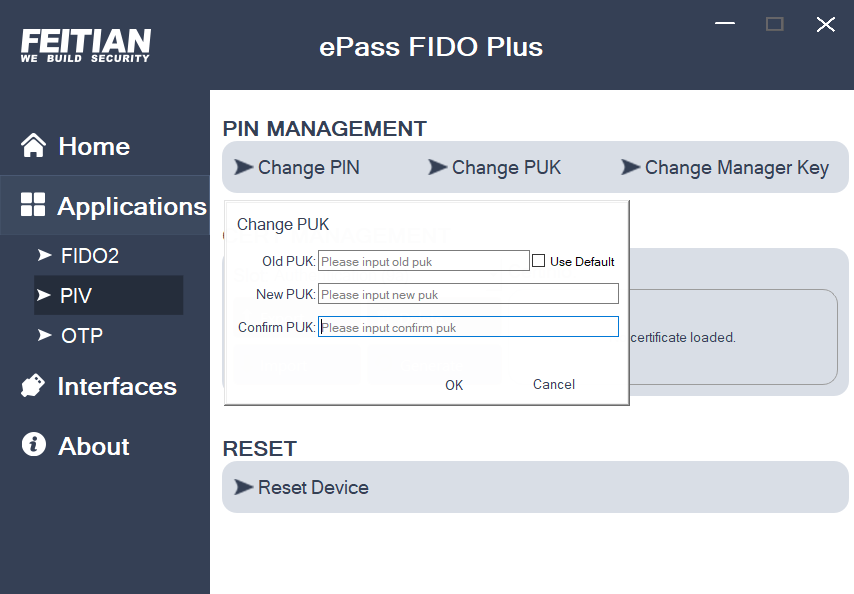
Change PUK
- PUK is a permission setting above PIN in PIV that supports modification, and the default PUK code is 12345678. Unlock the PIN via the PUK when the PIN locks up. Note that the PUK length limit must be 8 digits. The default retries for PUK is 3. Modifying the PUK must meet the PIV requirements, as shown in the figure below.
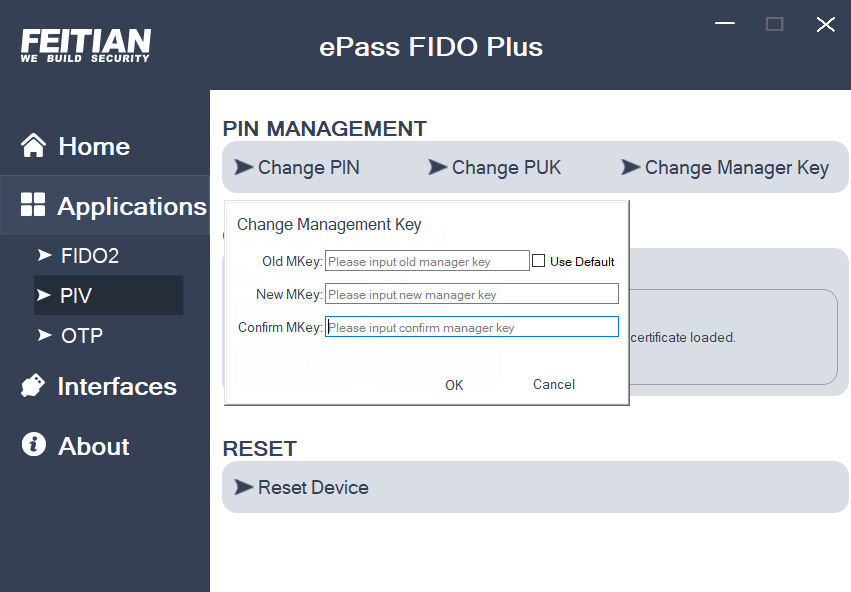
Change Management Key
- Manager Key is the equivalent of the administrator key of PIV. User needs to provide Manager Key to do operations such as generating certificates. User could modify Manager Key through our management tool. The default Manager key is 313233343536373831323334353637383132333435363738, modifying Manager key must having PIV PIN verified. The Manager key must be 48 digits in length. Modifications must meet the length requirements.
PIV Certificate BioPolicy
For devices that support fingerprint functions such as BioPass FIDO2, user can set BioPolicy and use fingerprint as another verification methods.
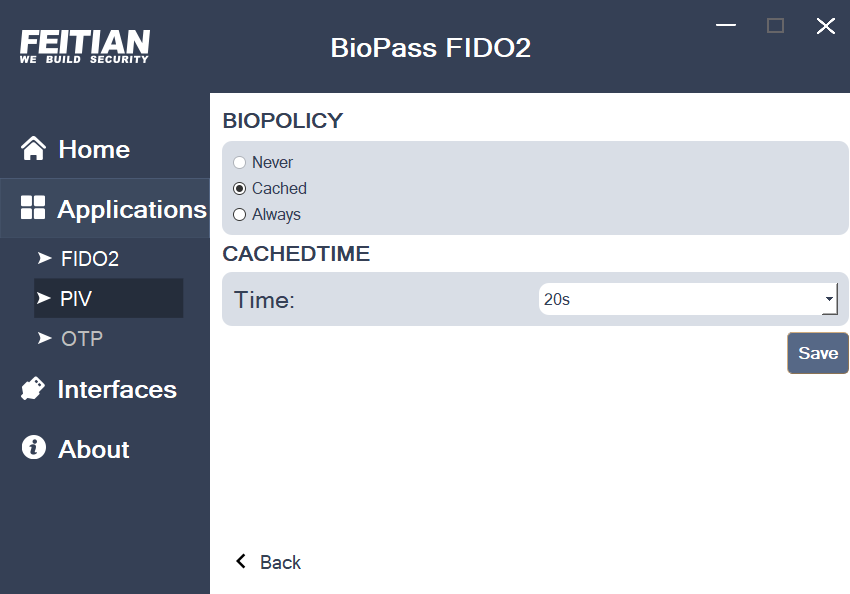
First, select the slot you want to set BioPolicy in(Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)), and then click “BioPolicy” to enter the configuration page. Configurable options are:
- “Never” : Does not support fingerprints.
- “Cached” : Supports cached fingerprints. The caching time could be set from 20s to 60s, default is 60s.
- “Always” : The fingerprint is needs to be verified every time to use.
PIV Generate Certificate
- Select slot (Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)), Click “Generate” to enter the configuration page. First configure the basic information of the certificate, including the type of certificate, request mode, and issuer information. After the configuration, click “Generate”. You still need to verify PIN and Manager Key. If not modified, you can use the default PIN or verify Manager Key.
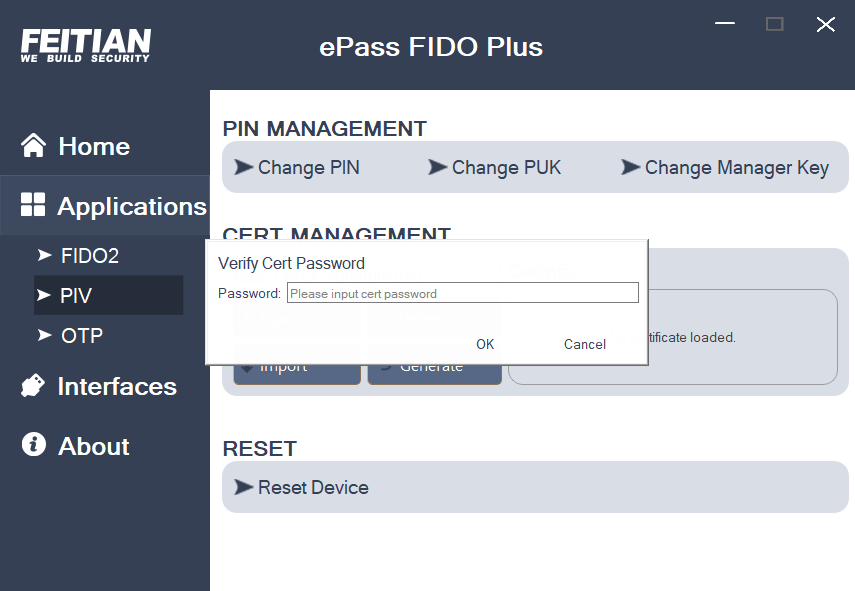
PIV Certificate Import
- Select slot include Slot (Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)), then click “Import” and choose a certificate in local machine. This process needs to verify PIN and Manager Key, If not modified, you can use the default PIN or verify Manager Key, if the certificate file has a password, you also need to enter the password of the certificate file.
PIV Certificate Export
- Select slot (Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)), then click “Export”. Exporting a certificate requires you to configure the exported path information and then complete the certificate exporting.
PIV Certificate Delete
- First select the slot include Slot (Authentication (9a), Digital Signature (9c), Key Manager (9d), Card Authentication (9e)), click “Delete”.
- Deleting a certificate requires verification of PIN and Manager Key, If not modified, you can use the default PIN or verify Manager Key, if success the certificate in that slot will be removed.
PIV Reset
- PIV Reset is mainly use to recover the number of retries of PIN and PUK , set PIN, PUK and manager key to default value, and delete certificate. Also considered as initialization.
PIV macOS Smartcard Log on
- For macOS, our products allows log on authentication through PIV. Please see link for detail steps.
OTP
OTP functions includes:
- Configuring HOTP, Static Password, Challenge-Response for supported devices/
- To configure TOTP, please use FT_Authenticator(Windows, Android and IOS) and FT_Personalization tool
- Deleting slot’s configuration.
- Swapping configurations between two slots(not available for devices that only support one slot) .
- For Windows, the manager tool supports different keyboard layouts. The specific configuration process is shown in the figure below.
Click “OTP” to enter the OTP page.
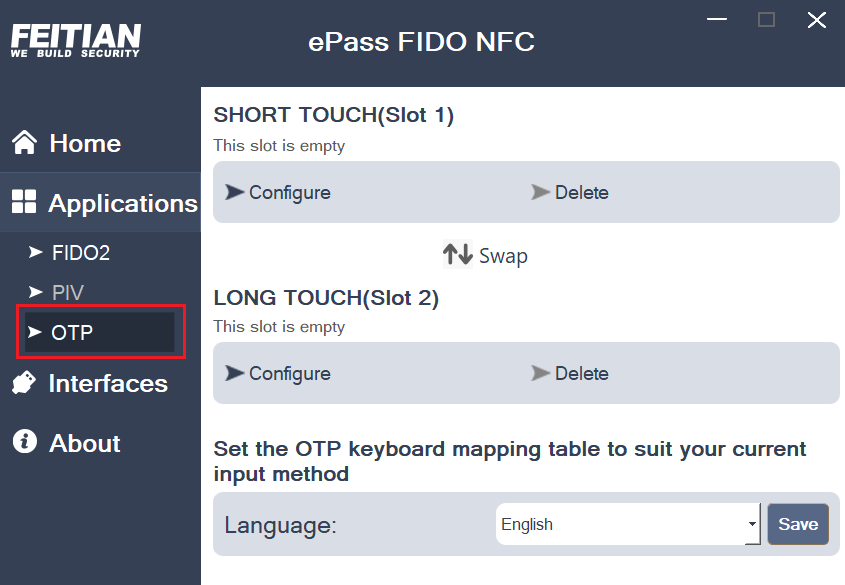
OTP Configuration
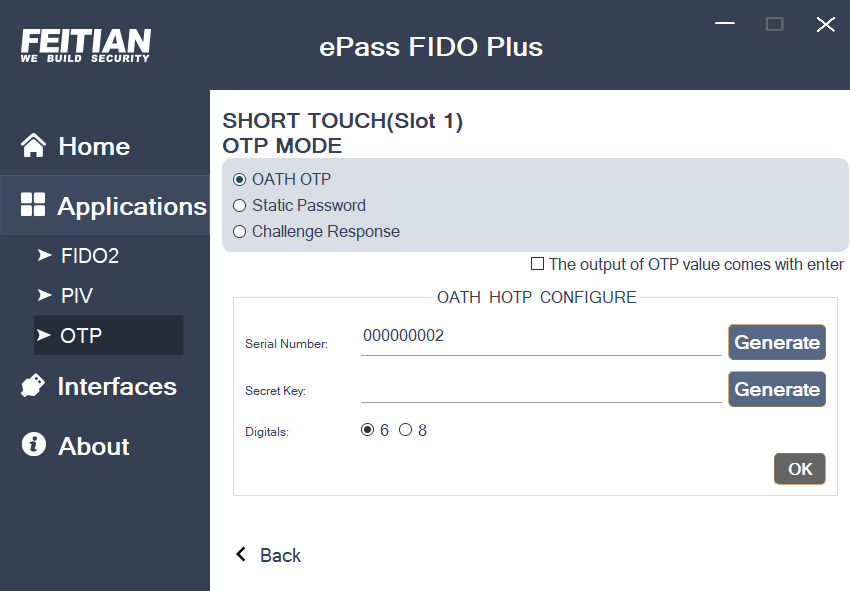
Select the Slot, and click the corresponding “Configure” to enter slot configuration page and start setting up your OTP:
- Select OTP mode: OATH OTP, Static Password, Challenge-Response.
- You can enable “The output of OTP value comes with enter”.
- The “serial number” displays the built-in serial number of the device by default, but also supports re-setting, click “Generate” to generate a random serial number, or input one(numbers and alphabets).
- The “Secret key” sets the configuration key. Generate a random order key by clicking “Generate” or input one(Hex).
- “Digitals” means the number of OTP digits and could be set as 6 or 8.
- Click “OK” after finish configuration.
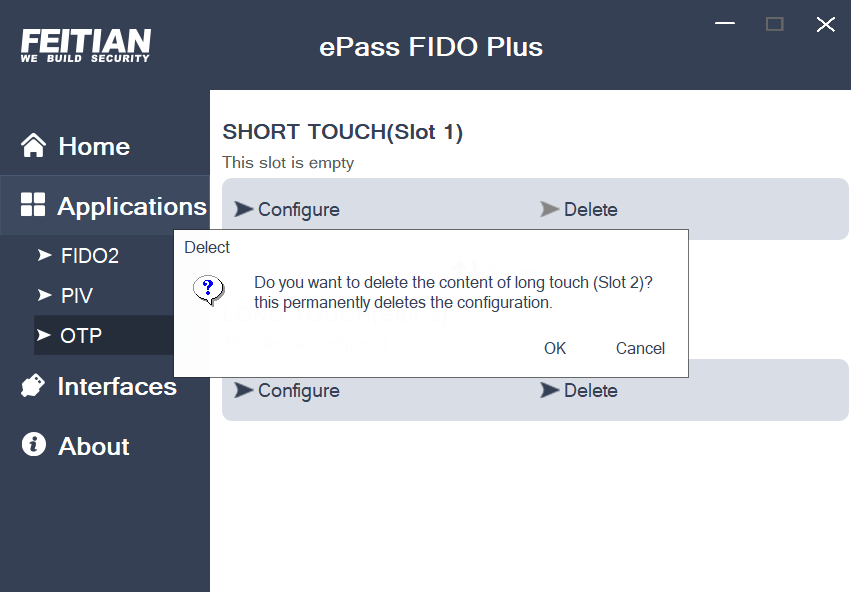
Note If the current configuration slot has already been configured, the tool will remind you whether to overwrite the configuration and make sure to continue.
If touching key is needed, the tool will prompted to touch the key, and a error will be returned if you didn’t touch the key in about 10s. After the verification succeeds, the personalization is successful.
OTP Swap
OTP Configuration supports the switching of Slot1 and Slot2 configurations by clicking “Swap” (Not available for devices that only have one slot).
OTP Delete
Select a Slot, to remove the configure, click the corresponding “Delete” and follow the prompt.
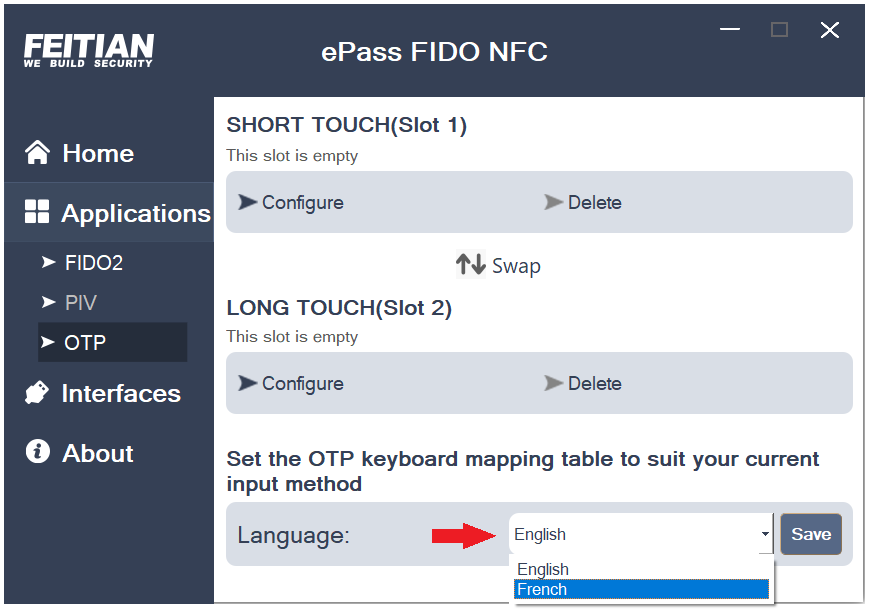
Change keyboard layout
- If a user have configured Static Password or HOTP using a non-English keyboard layout , the output OTP value will be invalid with the same keyboard layout.
- Our products are able to support different keyboard layouts(Currently supports English and French keyboard, more keyboard layouts will come soon).
- In order to change, go to the OTP page, open Language box, select one, and click “Save”.
- Please note that some version of your key may not support this functions.
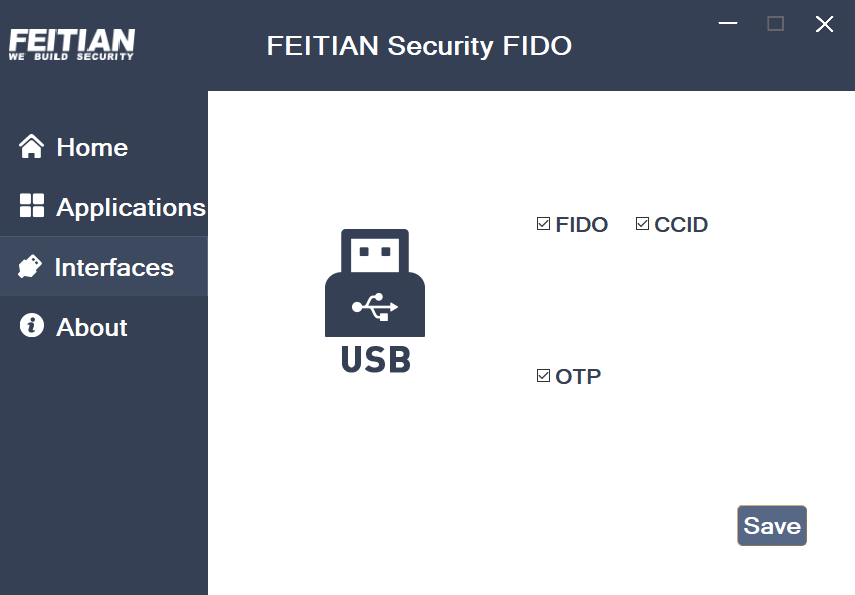
Interfaces
Our management tool provides function switching in “Interfaces” page.
Example:
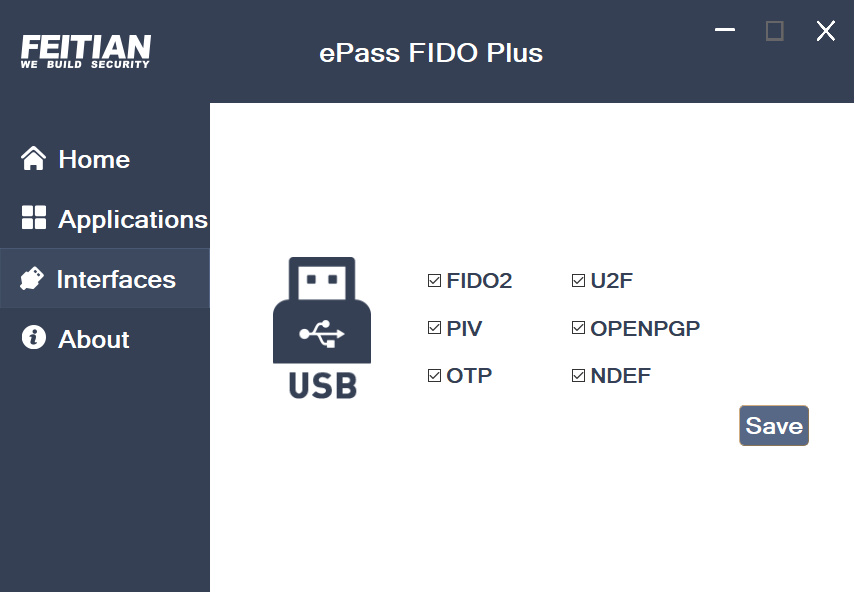
- For ePass FIDO Plus , supported function switching list: FIDO2, U2F, PIV, OTP, OPNPGP and NDEF.
- For ePass FIDO NFC , supported function switching list: FIDO, CCID and OTP, Note that at least one protocol must be retained.
Note that some products currently do not support function switching.
Click “Interfaces”, check the preferred functions and click “Save”, follow the prompted to re-insert the device, and wait to succeed.
ePass FIDO NFC interface:
ePass FIDO Plus interface: